
Recent high-profile cyberattacks on critical infrastructure and healthcare are a stark reminder of how vulnerable systems can be. Change Healthcare’s recent security breach, for example, created a backlog in claims and disrupted healthcare payments across the country.
Cyberattack perpetrators often demand a ransom to regain access to systems or, in the case of Change Healthcare, completely debilitate the organization’s revenue flow. These types of attacks are becoming more common and, for treasury and payments professionals, they’re the stuff of nightmares.
High-profile cyberattacks make clear an organization’s ability to conduct business is heavily dependent on its digital security. Protecting client and company data is crucial, and the stakes will continue to rise as the world becomes more digital. The prevalence of artificial intelligence (AI) could make attacks more systemic, increasing in frequency and impact.
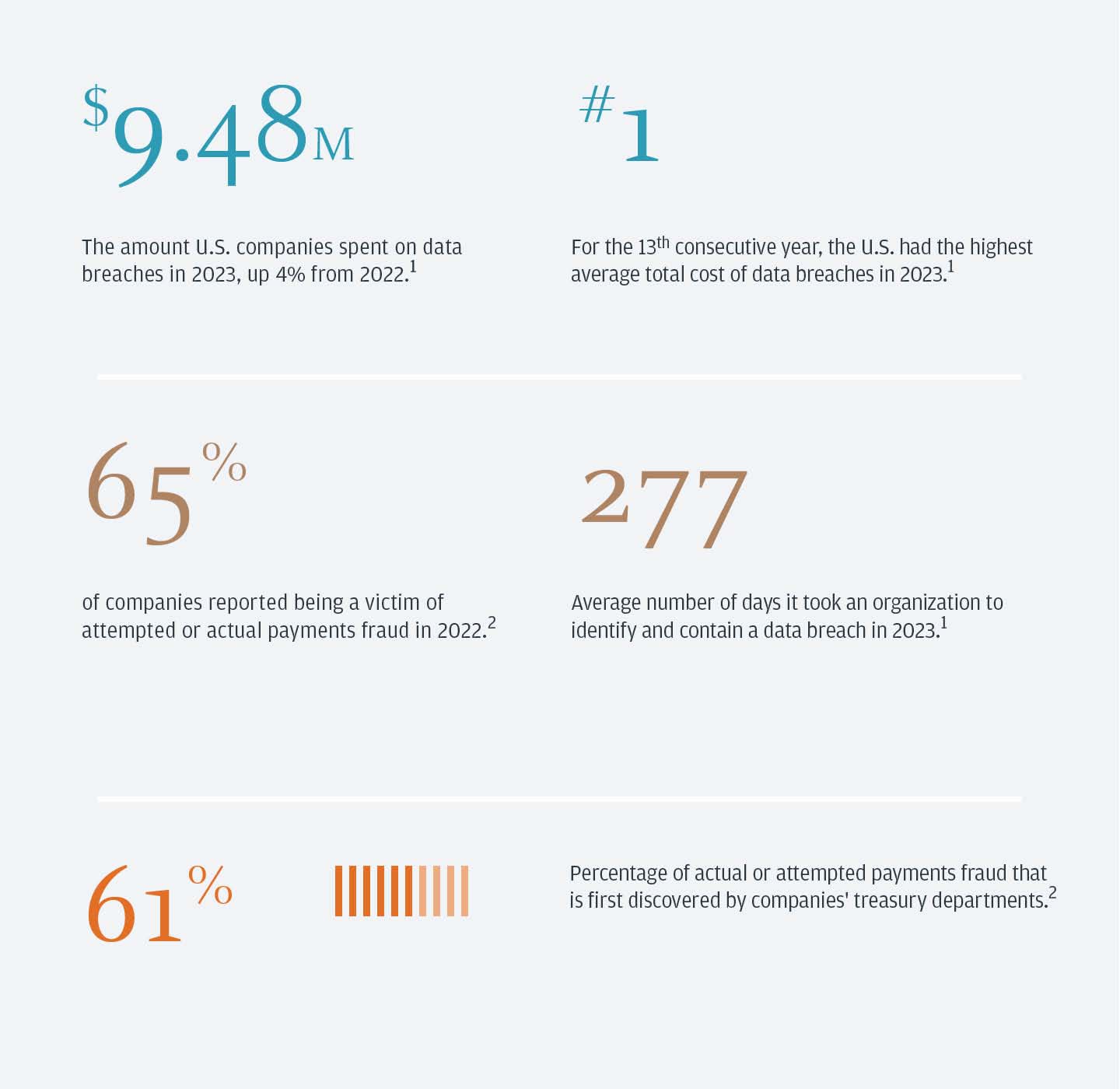
Data breaches cost U.S. businesses more than $9 million in 2022 and 2023,1 making cybersecurity a key, board-level focus. Organizations should create proactive and practical strategies to protect themselves, customers and other stakeholders.
Here are four key actions your business can take now to guard against a cyberattack.
1. Create a playbook
Creating a clear, comprehensive business contingency plan and cybersecurity policy could mean the difference between a thwarted cyberattack and one that hobbles your business.
To create your company playbook, start by identifying mitigation strategies across various scenarios. Then test those strategies. Consider the different access points and ways your business could be compromised. For example, cybercriminals could hack your servers or they could steal customers’ identities, which could be leaked, sold or held for ransom.
Strong cybersecurity policies are built through ongoing communication and cross-functional relationships across operations—leveraging the contacts, skills and experience of legal departments, business operations and HR. Once you know each business function’s most valuable assets, you can discuss how to protect them.
“You can have the strongest controls in the world, the best cybersecurity program—but one thing that organizations continuously need to work on is improving their crisis management processes.”3
JF Legault
Global Head of Cybersecurity Operations, J.P. Morgan
Part of your playbook may include creating backup systems in case a ransomware attack hijacks your primary ones. If you typically initiate critical wire payments through a company workstation, for example, you could use your bank portal or mobile app as a backup. This could mean providing staff a secure way to use their personal devices to make payments during an emergency.
2. Do table-top exercises
Table-top exercises are sessions where team members discuss their roles during an emergency based on various simulated emergency situations. These exercises can help you anticipate and work through weaknesses before a malicious event occurs.
A treasury team should be prepared to know which steps are critical to keep the business running. For example, if your customer database is hacked and held for ransom, your team may:
- Call law enforcement and the third-party negotiator.
- Identify your critical payments.
- Deploy pre-assigned, pre-approved individuals to use their personal devices to make critical payments.
- Call your bank and tell them to reprocess all payroll files from the previous week.
A clear communication plan for employees and the media is also key.
By working through various potential scenarios, your treasury team can keep payments and communication flowing, even if the rest of the business is under attack.
“It’s important to test resiliency plans at least twice a year with simulated drills and implement any necessary changes to ensure all employees are comfortable with processes and procedures.”
Adam Bulava
Head of Firmwide Technology Resiliency, J.P. Morgan
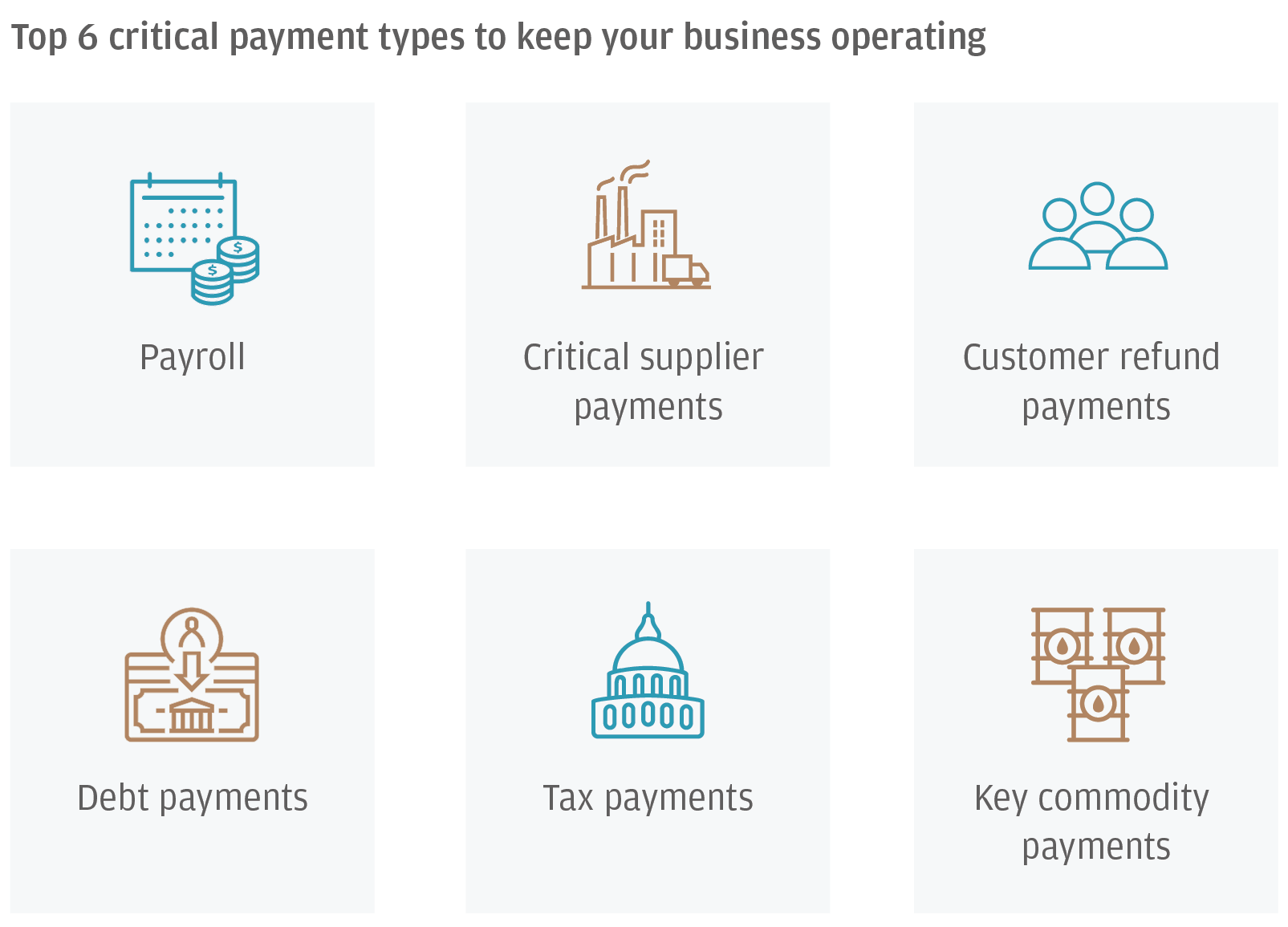
3. Identify your critical payments
Before you can secure critical payments in emergency situations, you need to know what your critical payments are. Treasury can identify which payments have to go out immediately and which can wait. That can save valuable time and team effort when a cyberattack takes place.
Say a hack occurs on Thursday, and payroll is on Friday. Because payroll is a critical payment and can prevent further distress and uncertainty for staff during a cyberattack, you should have a contingency plan to make that payment. You could use a third-party payroll provider or your bank’s previous payroll files. Debt payments must also be made to prevent your company defaulting on its commitments. Critical supplier payments are another aspect to consider to retain access to essential supplies and services.
4. Engage your business and banking partners
Educating all areas of your business about your cybersecurity strategy may help reduce vulnerabilities throughout your operations. Biannual anti-fraud training for staff, for instance, could be one of your company’s best investments. It’s critical that treasury staff are trained to identify and respond to cybersecurity threats. The vast majority of attacks happen through employees, whether they’re opening a malicious email or a leaving a company laptop in an unsecure location.
You should also engage your critical external relationships to prevent fraud, including external counsel, vendors, banking providers and insurers. From a treasury perspective, you might engage your bank to help protect your business. Fraud prevention services, such as address verification services (AVS) and ACH debit blocks, can help keep systems and processes flowing during a security breach or data leak.
3 tactics midsize businesses can implement to reduce digital risk
- Communicate important information about cybersecurity threats and best practices to employees through regular newsletters, trainings and meetings.
- Develop one-click reporting and tracking tools for visibility across operations.
- Build a recovery plan to outline how the business will resume operations following a cyberattack or other disruption.
Take the next steps to protect your business
Cybersecurity has a massive impact on a midsized business. Now is the time to ensure your business is equipped and ready to handle these threats.
Connect with your J.P. Morgan representative to learn more about our cybersecurity solutions.
References
IBM Security Costs of a Data Breach Report 2023
2023 payments fraud and control survey report, AFP
“Payments industry partnerships offers solution to growing cybercrime concerns,” The Fintech Times, September 2021. https://thefintechtimes.com/payments-industry-partnership-offers-solution-to-growing-cybercrime-concerns/
JPMorgan Chase Bank, N.A. Member FDIC. Visit jpmorgan.com/commercial-banking/legal-disclaimer for disclosures and disclaimers related to this content.







