In an era defined by accelerating cyberthreats and technological disruption, founders face a complex, evolving landscape. Regardless of industry, this is a reality for startups, whether they’re developing a first prototype, fine-tuning a go-to-market strategy or preparing to go public. The same advances in artificial intelligence (AI), cloud computing and automation that enhance companies’ defenses are simultaneously exploited by adversaries. On the horizon, quantum computing promises to reshape encryption and cryptanalysis, making data protection and offensive capabilities more powerful.
Staying ahead in today’s cyber landscape hinges on several factors, including enhancing cyber expertise within your organization or working with cybersecurity experts, strategically integrating AI while continuously revisiting and adapting its role in your organization and fostering a security-first culture that weaves together technology, processes and people.
The modern cyber landscape
The venture capital investment surge in U.S. cybersecurity startups that peaked in 2021 was remarkable, but not sustainable. Funding almost doubled that year compared to 2020, driven by a confluence of factors: the shift to remote work, high-profile security breaches and an abundance of capital seeking tech investments.
However, 2021 was an anomaly, not the norm. In today's market, there is a need for more tempered expectations, sustainable unit economics, and a clear path to profitability.
U.S. venture investment in cybersecurity startups by application
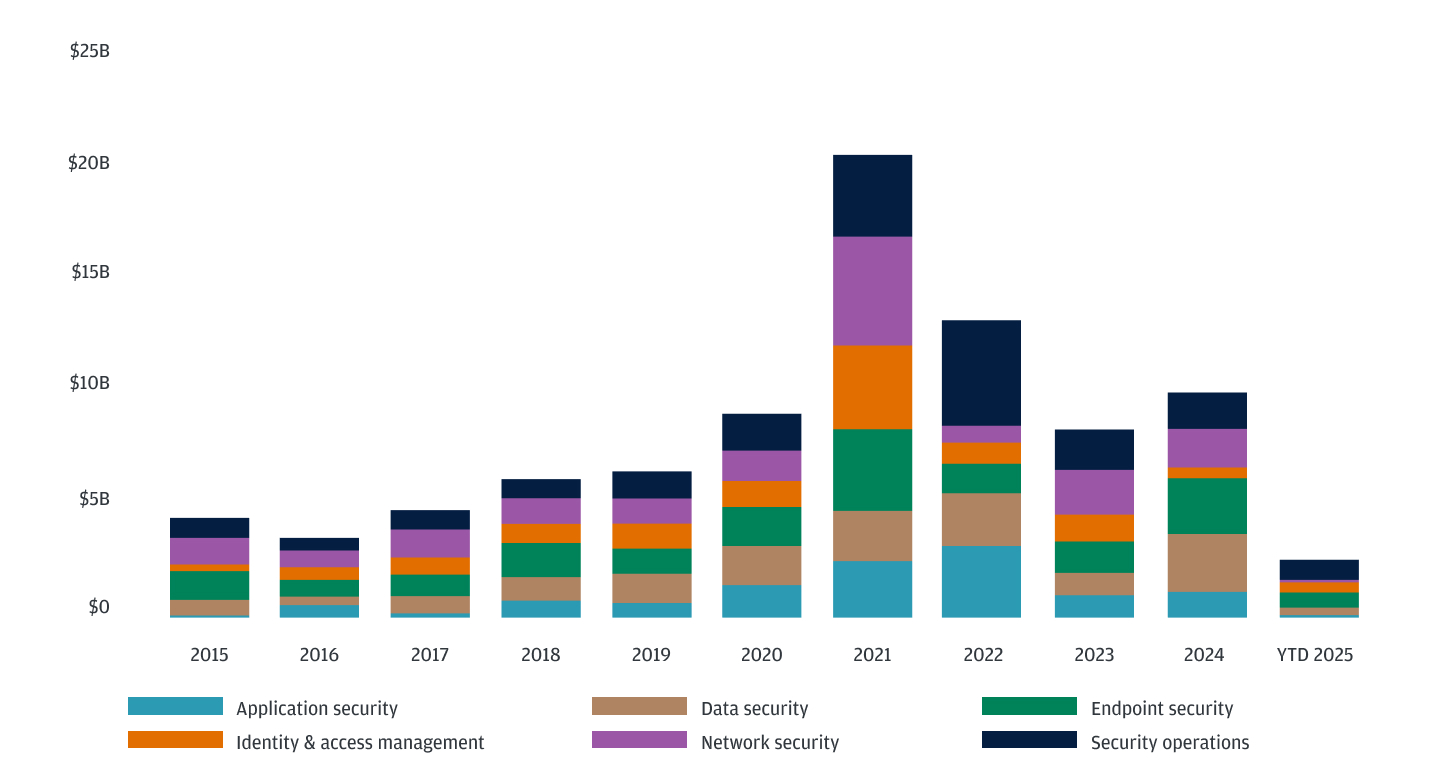
Source: PitchBook, YTD 2025 as of 3/31/2025
Despite the broader market pullback, certain cybersubsectors continue to draw consistent investment, notably identity and access management, network security and data privacy. These areas form the foundation of most enterprises' security strategies, receiving steady funding even when overall budgets are constrained. However, because they’re considered essential, competition in these foundational areas of cyber is intense. Founders who succeed in these categories set themselves apart through deep integration—whether by embedding into zero trust frameworks, automating compliance workflows or customizing solutions to meet the specific needs of regulated industries.
Meanwhile, both application and endpoint security have experienced gradual but meaningful growth since 2018. As applications increasingly serve as the new perimeter in software-native environments and hybrid and remote work models expand the number of devices in use, enterprises are keen to adopt solutions that integrate security directly into the development lifecycle or provide real-time protection for endpoints.
However, with the proliferation of specialized security tools, enterprises are facing the challenge of tool sprawl—managing multiple consoles, dealing with isolated alerts and navigating fragmented telemetry streams, all of which impede effective incident response. As a result, many buyers are now looking for unified platforms or interoperable ecosystems with a centralized dashboard, open APIs for data sharing and modular architectures. Startups that position themselves as ecosystem enablers—providing connectors, data fabrics and partnership integrations—distinguish themselves by reducing friction and speeding up the time to value for customers.
Harnessing AI presents opportunity and new risks
Perhaps the most transformative force in cybersecurity today is AI. Machine learning models can analyze terabytes of network traffic, user behavior and system logs in real-time, automating routine triage tasks and surfacing anomalies that rule-based systems miss. This enables security teams to focus on high value investigations and reduces the burden of false positives. By facilitating fluent collaboration between human security teams and automated systems, AI is redefining how organizations approach threat detection and response.
The increase in cybersecurity startups incorporating AI over the last decade reflects the growing recognition of its potential to revolutionize threat detection and response. While investment activity in terms of venture dollars has stabilized since 2021, deal count reached an all-time high in 2024, suggesting that AI-driven cybersecurity remains a focus area.
U.S. venture investment in AI-cybersecurity startups
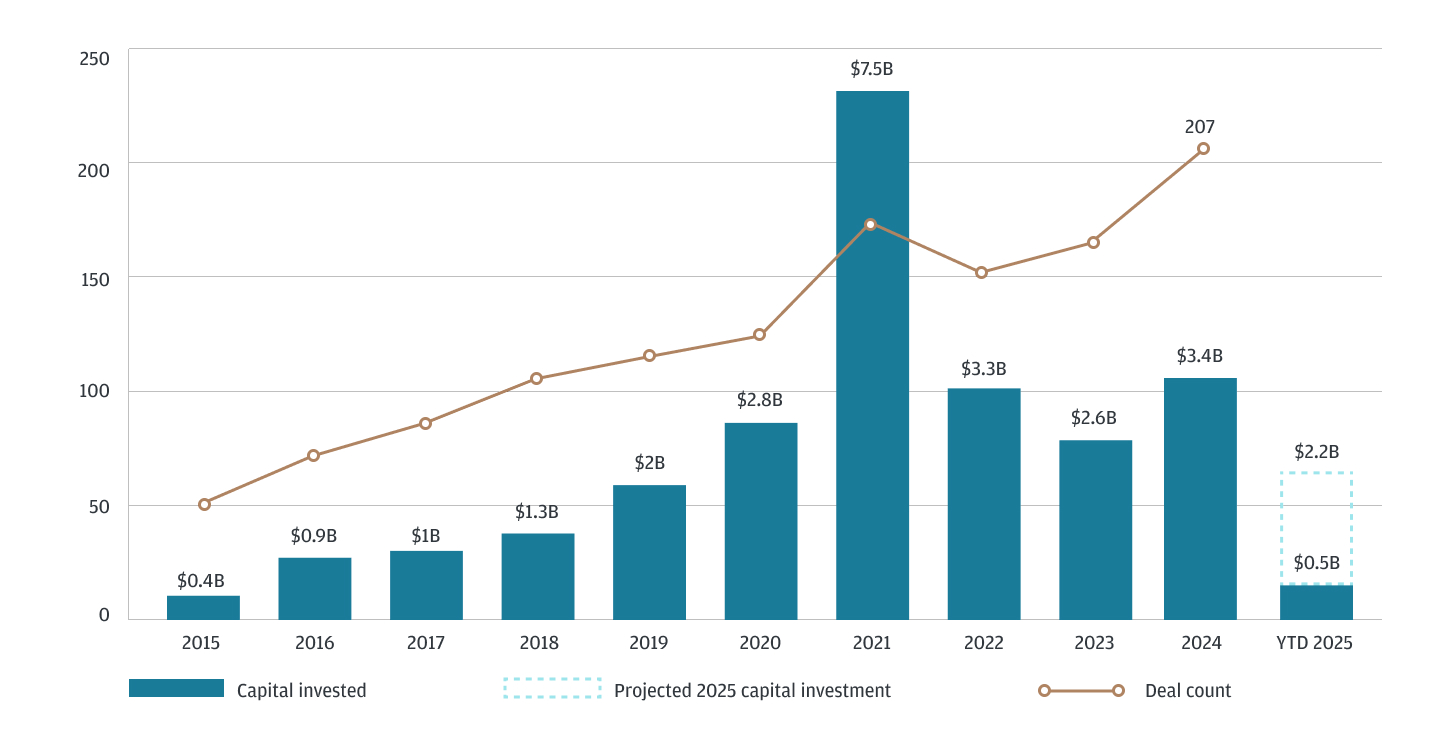
Source: PitchBook, YTD 2025 as of 3/31/2025
AI-driven security solutions help organizations detect and respond to threats in real-time, greatly enhancing their security posture. By utilizing machine learning algorithms, these solutions can process vast amounts of data to identify patterns and anomalies that may signal a cyberthreat, helping organizations stay ahead of potential attacks. For instance, a financial services company handling millions of daily transactions might rely on a traditional security system that flags suspicious activity based on predefined rules, potentially overlooking new cyber threats. In contrast, an AI-driven cybersecurity solution can analyze extensive real-time transaction data, identifying subtle anomalies, such as a hacker using compromised credentials to execute microtransactions that evade traditional fraud detection.
"AI agents can be weaponized by hackers to scale up the number of potential attacks by many orders of magnitude,” said Jon Sakoda, founding partner of Decibel VC. “Savvy red teams can now leverage the power of AI clusters to knock on every door, search for every exploit, and eventually find the weakest point of vulnerability. Defenders need to evolve from checklists to code, and ultimately build a programmable defense to respond to these modern AI-driven attacks.”
However, integrating AI into cybersecurity comes with its own set of challenges. Enterprises must address complex issues related to data privacy, algorithmic bias and the ethical use of AI technologies.
Potential AI-cybersecurity applications and considerations for enterprise leaders
| Applications | Considerations |
|---|---|
| Real-time threat detection and response | False positives may overwhelm security teams if not fine-tuned properly. |
| Automated phishing and malware detection | AI models can be tricked by adversarial attacks or manipulated inputs. |
| Behavioral analytics for insider threat detection | Privacy concerns may arise from continuous monitoring of employees. |
| AI-driven security automation (e.g., patch management, vulnerability scanning) | Over-reliance on automation may lead to blind spots if human oversight is reduced. |
| Fraud prevention in financial transactions | Algorithmic bias could lead to wrongful transaction blocks or account freezes. |
Adversaries are innovating, too
While AI offers significant advantages in defense, it also presents new challenges as cybercriminals harness its capabilities to enhance their attacks. AI can automate reconnaissance, craft personalized attacks and even adapt to changing security measures, posing significant challenges for traditional security frameworks. The real threat lies not just in automation but AI's ability to adapt continuously, enabling AI-driven malware to modify its tactics mid-attack, selecting the most effective methods to infiltrate, escalate privileges and evade detection.
“Savvy red teams can now leverage the power of AI clusters to knock on every door, search for every exploit, and eventually find the weakest point of vulnerability.”
—Jon Sakoda, founding partner of Decibel VC
Building a resilient enterprise
Understanding the multifaceted nature of cybersecurity is crucial for organizations navigating the evolving threat landscape. AI plays a dual role, offering powerful tools for both defense and offense, but it is not a cure-all. Business leaders must recognize that a comprehensive cybersecurity strategy involves more than just technology. AI can enhance threat detection and response, allowing organizations to swiftly and accurately neutralize threats. However, relying solely on AI can leave security gaps, as cybercriminals continuously adapt and exploit vulnerabilities. In light of this, founders can take varied approaches.
- Cybersecurity startups can focus on verticals where there’s clear, demonstrated demand for security solutions—areas with well-established pain points and proven use cases. Differentiation will likely come from addressing these needs with deep, domain-specific integration and ecosystem partnerships. If you’re building AI features, prioritize transparency, explainability and resilience against adversarial attacks.
- Enterprise founders seeking security solutions may treat AI as a powerful enabler—not a cure-all. It can accelerate detection, reduce response time and augment human decision-making, but it’s not a standalone fix for systemic security challenges. Vet vendors for clear metrics such as mean time to detection, false positive rates and patch deployment speed. Insist on tools that interoperate with your existing stack while still supporting human-in-the-loop controls.
- All founders can cultivate a security-first mindset across the organization. Align technology investments with regulatory and industry priorities, invest in continuous education, and integrate security into every phase of product development and operations.
Build your future with J.P. Morgan
We are dedicated to helping your startup enhance cybersecurity and safeguard against fraud. J.P. Morgan Innovation Economy Startup Banking can help find the best solutions for your business.
JPMorgan Chase Bank, N.A. Member FDIC. Visit jpmorgan.com/commercial-banking/legal-disclaimer for disclosures and disclaimers related to this content.