- Credential stuffing. In this case, bad actors gain access to usernames and passwords through data breaches, which have occurred at large telecommunications and social media companies in recent years. Because people often use the same usernames and passwords across numerous websites, criminals attempt to use those credentials to access financial accounts. They may also leverage personal information shared online to get past security questions or quickly guess passwords.
- Impersonation scams. Cybercriminals may also impersonate an individual or the friends, family members or acquaintances of an individual, then leverage that person’s identity to commit fraud.
Enhanced voice impersonation capabilities of artificial intelligence have increased the risk and frequency of impersonation scams.
- Confidence and romance scams. In another form of impersonation, bad actors cultivate a relationship with a high net worth individual under the guise of being a friend or romantic interest. The communication inevitably leads to a request for money, often to help the alleged connection out of a tough time or perhaps invest in a business or project.
Each type of cyberattack can put your family’s finances at risk, whether it’s through gaining unauthorized access to accounts or money for fraudulent projects or people. As noted, the issue often begins with the criminals’ access to personal information through a breach, social media activity, video game chat or other websites.
Reputational risk is another consideration for families. Family members active on social media can inadvertently share information that potentially damages the family business or the family’s hard-earned reputation and can even lead to financial fallout. What’s more, generational differences often mean that family members have differing views regarding the use of social media.
It’s impossible to fully avoid social media gaffes, especially if you’re teaching adolescents how to manage their digital life. People will make mistakes. However, a family social media policy can reduce the potential for problems – and provide context for how individuals make decisions about their social media sharing and managing security protocols. Here’s how to create a policy that helps reduce your family’s social media risk.
Start with the why
As you begin to discuss what a social media and digital device policy entails, ask your family members some critical questions:
- What does our family stand for and value most?
- Why is developing strong digital footprint skills important?
- How do we want to use social media?
- Why is online security important to us?
- How can we be intentional about spending the right amount of time on social media and digital devices?
- What do we want to highlight or avoid?
For instance, one family agreed that family members or friends along for the journey would avoid sharing news online of big purchases, events attended or activities related to their vacations. Because they value privacy and quiet demonstration of financial wealth, they agreed to avoid posts that highlight material abundance. Rooting your policy in values can make it easier for people to determine whether shared information reflects those values or goes against them.
Another family, with teens, tapped into resources on Common Sense Media to collectively explore healthy screen time habits and how best to navigate the effects of social media on mental health. Armed with new insights, they incorporated practices into their policy to take advantage of the benefits technology can offer while putting in safeguards to minimize the risks.
Understand the risk
As mentioned earlier, generational differences could underscore a divide on views regarding social media use. Spend some time discussing how and why each party uses social media and the associated risks that may come with their use. Exploring these hypothetical dangers can help family members identify potential scams or trouble. Consider bringing in an expert to help you understand and secure your online presence.
Create the policy together
Work together as a group – perhaps as part of a family meeting – to discuss what the family is comfortable with sharing. Some families use the “grandma rule,” which recommends that you only post things you’d share with your grandmother. Prohibiting posts about family financials is also smart, and the same goes for posting about the family members’ current locations. For instance, some families’ social media policies request that people post about vacations only after they get back from their trip(s).
Your policy may also require family members to coordinate with the appropriate person within the family business before posting about the business; this touchpoint provides an added layer of scrutiny and security. Additionally, it’s important to understand that different people may have different comfort levels – aim to build an approach that works for the whole group. Don’t shortcut the process, either, as collaborating on this policy is a relevant, practical opportunity to build group decision-making skills.
Establish security expectations
Each type of social media platform has different privacy and security settings, but you can still create general rules to help family members better secure their online lives. Refer to some core practices below:
- Review social media or app privacy settings. Review these settings can help you understand what information is being collected. Adjust the settings to your preference and to maintain your privacy.
- Review permissions for third-party apps and artificial intelligence (AI) model learning.
- Create and manage passwords wisely. Create strong passwords and consider using a reputable Password Manager:
- Some families use simple passwords (e.g., years that mean something to you, pet names, etc.).
- Make sure these passwords are strong and complex: They should be at least 16 characters, using upper and lowercase letters, numbers and symbols. Consider using a unique password for each account.
- A reputable password manager with state-of-the-art encryption can help you organize your passwords and stay secure.
- Screen your invites and friend requests. Do not accept invites from people you do not know, particularly if you have not met them in person. Hackers and criminals generally look for an easy in to get personal information that they can use to take advantage of you and your family.
- Keep your posts and videos private. Post later or after you have left the destination. Do not tag your location, either, as this can divulge too much information.
- Avoid using public Wi-Fi. Never use public Wi-Fi to enter personal credentials on a website; this is one way hackers can capture your data. When public Wi-Fi cannot be avoided, use a virtual private network (VPN) to help secure and encrypt your session.
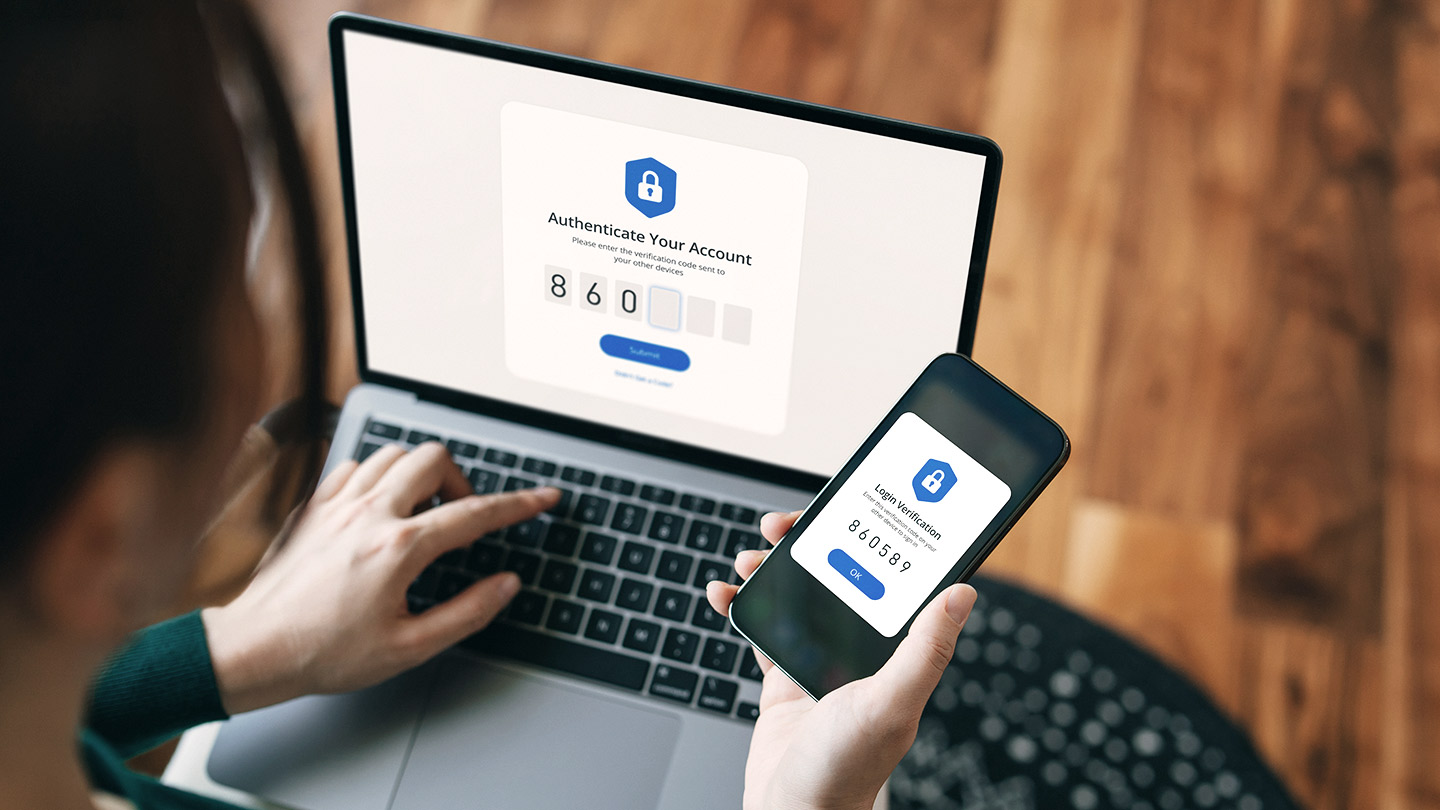
- Add an extra layer of security. Enable Multi-Factor Authentication (MFA), as it adds an extra layer of security by requiring a second form of verification (i.e., a code from an authentication app.
- Use MFA wherever it’s offered, such as social media, financial accounts, health care, etc.
You may also establish rules for whom individuals can follow or interact with online, such as limiting social media interactions to only people family members know in real life. Another possible guideline is to limit comments to only posts that originate from close friends or relatives. You may also restrict younger relatives from communicating with people they don’t know via video game chats or direct messages.
Create pre-posting questions
Providing family members with a series of straightforward questions to ask before they post can take the guesswork out of whether the information is shareable. For example, you may request that individuals consider:
- Does this post reflect our family’s values?
- Is this information personal, sensitive or proprietary to our family or family business, and could it be leveraged to commit fraud?
- Does this post reveal my exact location in real time?
- Does this post include others, and do I have their permission to post?
Establish accountability
Even with a policy in place, mistakes can happen. Use your social media policy to create responsibility for social media posts and accountability for when things go wrong. And although one’s digital footprint typically lives on regardless of whether the post has been taken down, you can use these moments to encourage family members to be more prudent with what they share online moving forward.
Consider the implications that major life events can have on your policy. After a new spouse innocently posted happenings about the family business that was uncomfortably viewed as an overshare, one business family now makes a point of meeting with each fiancé to share their social media policy, gather input and provide the opportunity for the soon-to-be married family member to ask questions.
Another family preparing for a private business sale that would soon hit the news held an all-family meeting to review and discuss their social media policy as the upcoming sale approached. In particular, the business owner wanted to share lessons from his friend’s experience; his friend, also a business owner, had a daughter who proudly linked to a news story showcasing the sale of her family’s business. However, this not only led her social circle to the news itself but inadvertently to the large sales price of the company, which was also included in the article.
Sharing personal information online is easier now than it’s ever been, and mistakes can lead to real-life consequences. By creating a social media policy for your family and reviewing it both annually and as life events happen, you can limit you and your family’s exposure to the risks of social media, thereby ensuring that online sharing doesn’t negatively affect your family’s finances, business or reputation.